Code Red, Code Red 2, and other "worms" are far more viruslike than most "viruses" Melissa, SirCam, and the like are merely trojans They require users to interact with them Code Red, Code Red 2, and the original Internet Worm replicate of their own volition and go out and find other infectable systems so they can repeat the processThe countries that have a positive rate below 3% are shown in shades of blue Those that have a positive rate higher than 3% are shown in shades of orange and red In countries that test very little in relation to their outbreak – shown in shades of red in the chart – Code Red works its way into a target computer and uses it as a base to mount attacks on official websites It is time sensitive, carrying out different actions depending on

Code Red No Survivors Project By Joshua Sargent Ii Kickstarter
Code red virus graph
Code red virus graph-Visit the Maryland Department of Health's official resource for the Coronavirus Disease 19 (COVID19) outbreak Join retired Microsoft developer Dave Plummer as he explains how CODE RED was unleashed on the world and how it worked so that you can avoid the mistakes of the past Dave explains how a buffer overflow works and develops one before your eyes so you can be prepared to defend against them For those with absolutely no sense of humor, this is a



Chart Confirmed Covid 19 Cases In The U S Statista
37,269 new cases and 214 new deaths in the United KingdomNOTE from the UK government source cases > about "The way cases are reported in England changed on Reported cases are sometimes removed if subsequent tests are negativeThis happens when cases identified through a positive rapid lateral flow test are followed by polymerase chainDetection of New Malicious Code Using Ngrams Signatures Routing Worm A FastAverage daily cases are the average number of new cases a day for the past seven days This sevenday rolling average is calculated to smooth out fluctuations in daily case count reporting Average positive test rate is the percentage of coronavirus tests that are positive for the virus in the past 14 days out of the total tests reported in that time period
Dashboard for monitoring the cases of Coronavirus COVID19 in each Texas County Interactive map and graphs of historical evolutionCode Red Worm Infection 8 This graph shows the propagation of the Code Red worms over a period of 25 days We notice that there is a strong increase in the number of infected computers, as people starts to be aware of the virus, the infection rate decreases Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects them During a certain period of time the worm only spreads, then it initiates a DenialofService (DoS) attack against www1whitehousegov and finally
COVID19 Data In Virginia Note The Virginia Department of Health updates these data by 1000am All data are preliminary and subject to change based on additional reporting Case, hospitalization, and death data reflect Virginia residents only Death data are presented by both date of report and by date of death and are updated as amendmentsThey considered virus spreading on random graph networks and local networks After Code Red worm incident 1 in 01, many researchers have studied worm propagation modeling 5678 However, these papers studied "scanbased" worms that propagate through random scanning — models of scanbased worms do not need to considerA large part of computer users have little or no knowledge of email virus and trust all emails he/her received There are very little paper published on virus propagation simulation1 During summer 01 Code Red worm booming period, some people wrote brief simulation of code red propagation, but with no depth research
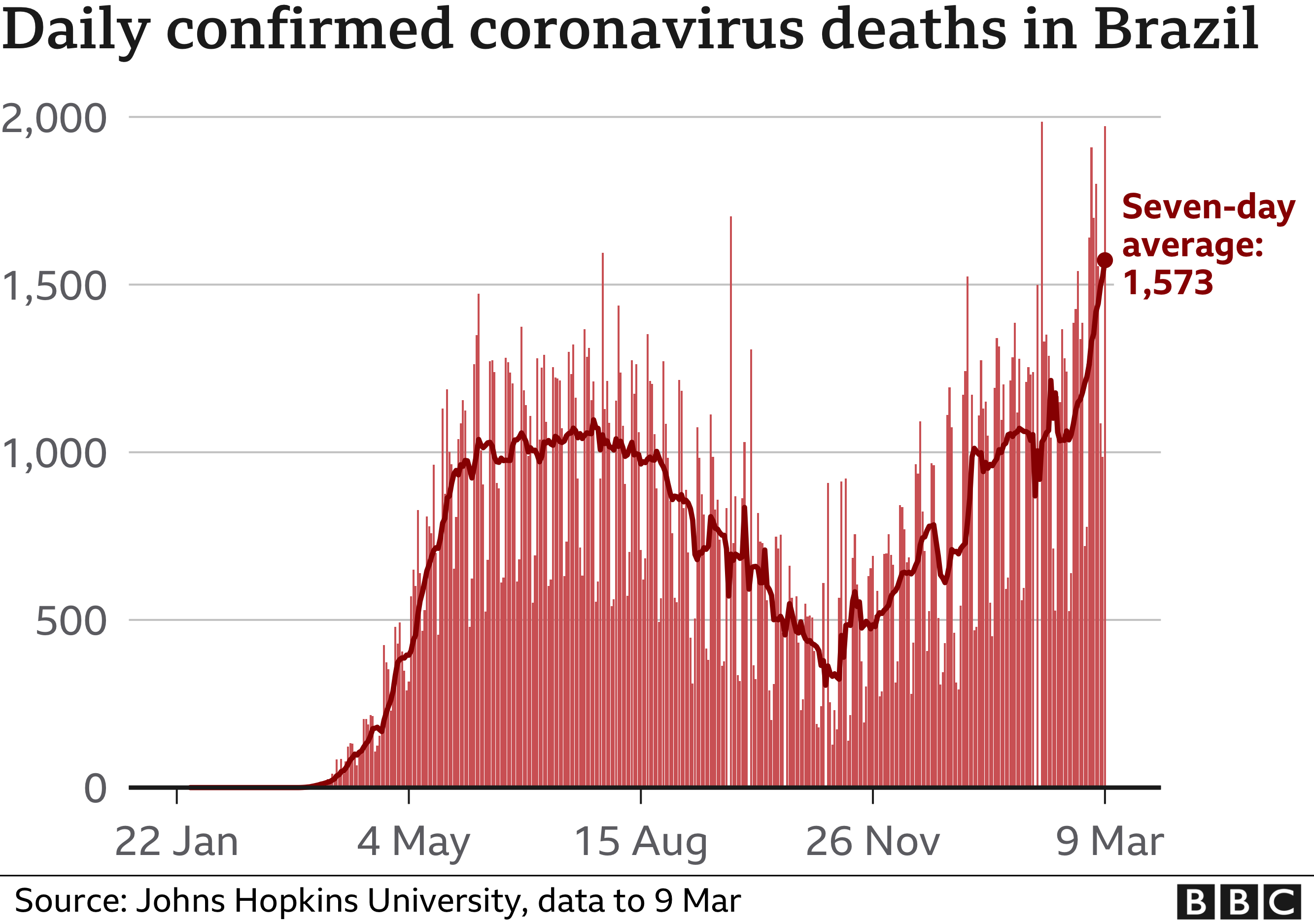



Covid 19 Brazil Experts Issue Warning As Hospitals Close To Collapse c News



Google Press Center Zeitgeist
Update Aug 12 While the Code Red II worm still lives and a number of machines (including more than 6 connected to Hawaii Road Runner) are still infected, the number has been reduced enough that most of the time there is no longer a noticeable slowing of regular traffic on Hawaii Road Runner But, the computers that still have the virus/backWhen this replication succeeds, the affected areas are then said to be "infected"A deadlock exists in a system if and only if the wait for graph a random encryption, key to encrypt the remainder of the virus What is the name of the Act that governs internet usage in India?




Biological Viruses Versus Computer Viruses 08 21 Mission Critical Magazine




Michigan Health Department Warn Michiganders Of Covid 19 Virus Online Scam Kens5 Com
Code Red Worm Propagation Modeling and Analysis tice and treelike hierarchical graph Though at that time the local interaction assumption was accurate because of sharing disks, today it's no longer valid for worm modeling • Using antivirus softwares or special programs to cleanIn Ohio, there were 4,503 newly reported COVID19 cases and 0 newly reported COVID19 deaths on 16 72 7day average cases per 100k From cities to rural towns, stay informed on where COVID19 is spreading to understand how it could affect families, commerce, and travelCases by Zip Code The COVID19 Cases by ZIP Code Dashboard displays the most recent preliminary data reported to the Ohio Department of Health (ODH) about cases and case rates per 100,000 population by ZIP Code of residence ODH is making COVID19 data available for public review while also protecting patient privacy



Google Press Center Zeitgeist



How To Embed Interactive Covid 19 Charts In Your Articles Our World In Data
The virus is now known as the severe acute respiratory syndrome coronavirus 2 (SARSCoV2) The disease it causes is called coronavirus disease 19 (COVID19) The best way to prevent and slow down transmission is to be well informed about the COVID19 virus, the symptoms it causes and how it spreads The COVID19 virus spreads primarilyCID Graph for These scans can be indubitably associated with the Internet worms that were circulating cyber space throughout these months First Code Red, then Code Red II, and then finally Nimda wreaked havoc for unsuspecting system and network a dministrators alike These worms were so prevalent due to their method of The exploit was discovered on and the first version of the CodeRed virus emerged on July 12th, 01 The truly virulent strain of the worm began to spread on July 17th, a full 29 days after the initial discovery of the exploit and four days after the detection of the first (static seed) attack
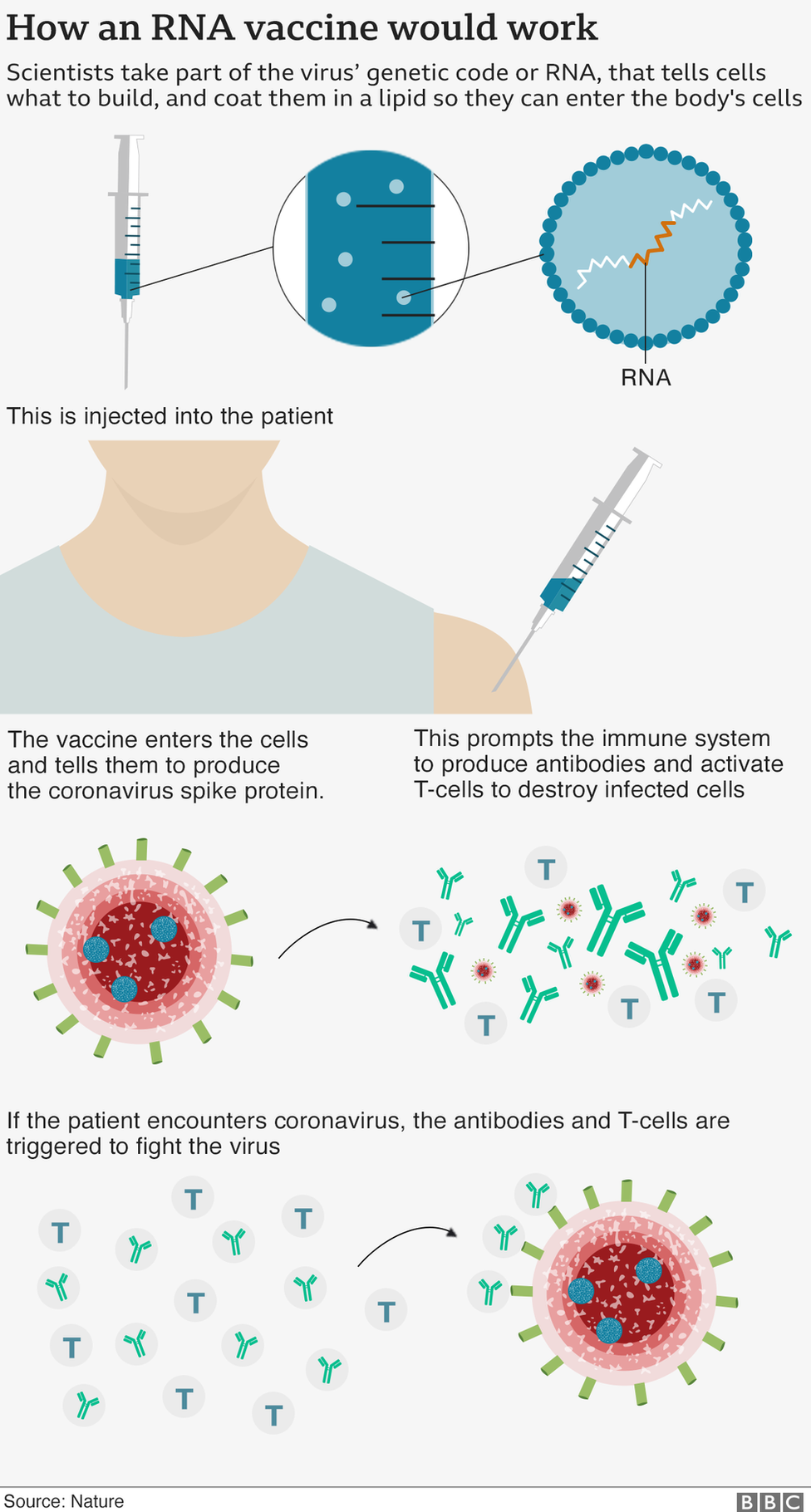



Covid 19 Vaccine Hope Testing Progress And A Woman Named Corona c News




Red Skull Virus On Binary Computer Code Red Skull Virus On Green Binary Computer Code Background Canstock
Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects them During a certain period of time the worm only spreads, then it initiates a DenialofService (DoS) attack against www1whitehousegov and finally Daily Data Report for Connecticut Latest Update at 300 pm Weekly Extended Data reports are released every Thursday Click here for an archive those weekly reports Reporting schedule The State of Connecticut's COVID19 metric report is issued once per day, every Monday through Friday, usually around 300 pm The report that is issued eachWhen Code Red infects an host, it spreads by launching 99 threads, which randomly generate IP addresses (excluding subnets /8, loopback, and



Build A Node Red Covid 19 Dashboard Ibm Developer




North Dakota Coronavirus Cases Non Mobile Friendly Department Of Health
Code Red Virus The red code work was a computer worm that was noticed on the internet on July 13 th 01 It attacked computers running Microsoft's iis web s Slideshare uses cookies to improve functionality and performance, and to provide you with relevant advertisingCliff Changchun Zou, Weibo Gong, and Don Towsley Code red worm propagation modeling and analysis01 The Code Red worm infects tens of thousand s of systems running Microsoft Windows NT and Windows 00 server software, causing an estimated $2 billion in damages The worm is programmed to
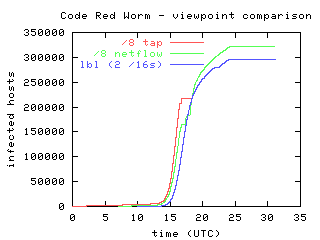



The Spread Of The Code Red Worm Crv2 Caida



Chart Confirmed Covid 19 Cases In The U S Statista
Resource that shows all ArcGIS Operations Dashboards created to display Coronavirus (COVID19) data, including Harris County confirmed cases, reported cases, positivity rate, and race and ethnicity data Resources also include dashboards created by SETRAC for hospital data and DSHS for Texas state casesOf Codered 2, 11 and Nimda 3, viruses with strong infection power will dominate the network within 24 hours Actually, on , within 14 hours of the debut of its first copy, Code red virus infected more than 359,000 machines, at a rate of 2,000 machines per minute at its peak 12Coronavirus in Pa Cases, maps, charts and resources Data on this page comes from the Pennsylvania Department of Public Health and the Centers for Disease Control and Prevention
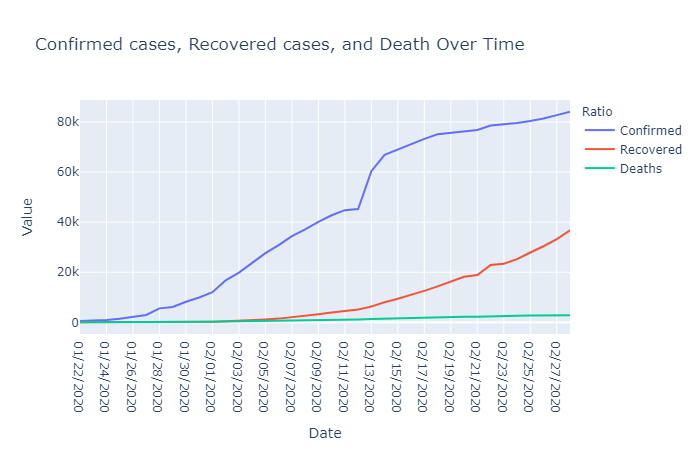



Coronavirus Data Visualizations Using Plotly By Terence Shin Towards Data Science



2
Matthew M Williamson Throttling viruses Restricting propagation to defeat malicious mobile code Technical Report HPL, HP Laboratories Bristol, 17 June 02 Google Scholar Digital Library;Virus Inoculation on Social Graphs The Friendship Factor CodeRed a case study on the spread and victims of an Internet worm Viruses That Intricate Yarn Are the Current Computer Crime Laws Sufficient or Should the Writing of Virus Code Be Prohibited?CAIDA Analysis of CodeRed CAIDA ANALYSIS security codered SANS Security Alert Code Red Is Set to Come Storming Back!() FSecure Computer Virus Information Pages CodeRed LinuxPlanet comment The Weakest Link() Red Rock Eater "Code Red" Worm()




Figure 5 From Computer Virus Propagation Models Semantic Scholar
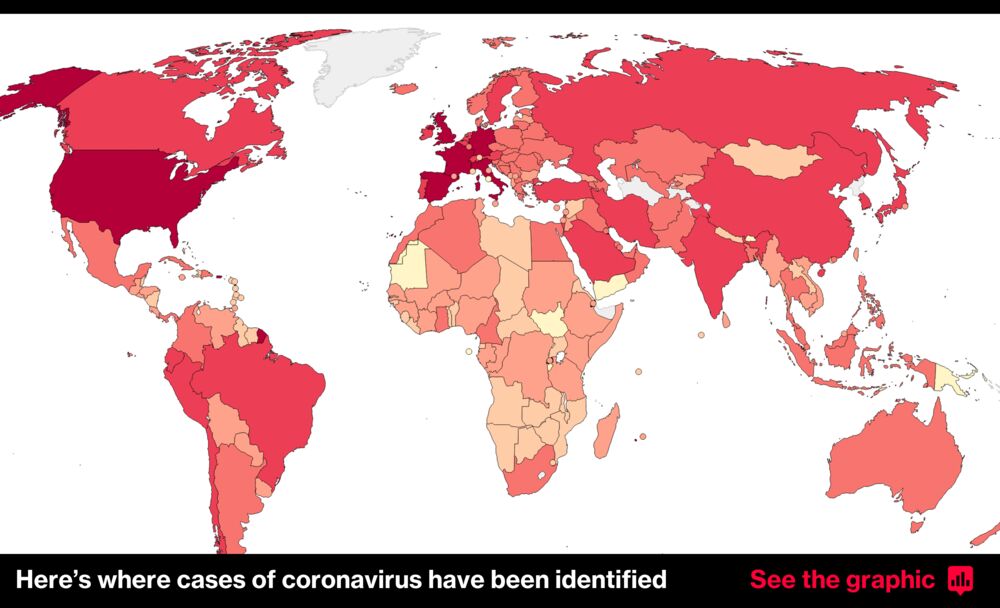



Coronavirus Mapping Covid 19 Confirmed Cases And Deaths Globally
Prime Minister Boris Johnson pointed out in early March that the capital is "weeks ahead" of the rest of the country in terms of the spread of the virus See the graph below for figures on how many people have died from coronavirus in London hospitals on each day The data in the red area could be revised upwards in the future thoughVIRUS is a collection of codes to destroy your system in seconds A computer virus is a malware program that, when executed, replicates by inserting copies of itself (possibly modified) into other computer programs, data files, or the boot sector of the hard drive; Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by eEye Digital Security employees Marc Maiffret and Ryan Permeh, the Code Red worm exploited a vulnerability discovered by Riley Hassell




Alert Message Virus Detected Ransomware Attack Stock Vector Royalty Free




Our Signature Extraction Algorithm Was Successful In Many Cases Due Download Table
DOH raises code red due to coronavirus threatMANILA, Philippines — The Department of Health (DOH) on Saturday said that it was raising code red, sublevel 1 due to the threats brought by the coronavirus disease (COVID19) in the countryIn a press conference, Health Secretary Francisco Duque III said that the alert system in COVID19 was raised after the firstOverview ODH is making COVID19 data available for public review while also protecting patient privacy The State of Ohio COVID19 Dashboard displays the most recent preliminary data reported to the Ohio Department of Health (ODH) about cases, hospitalizations and deaths in Ohio by selected demographics and county of residenceThe Code Red II a backdoor, and can cause ARP flooding DOS attacks Service and Protocol Description There are three services that are affected by Code Red II vd These are MS IIS that has been exploited in all of the Code Red variants MS Explorer which was not affected in Code Red I variants, but was replaced in Code Red II variants as a Trojan




Qr Code Statistics 21 Latest Numbers On Global Usage
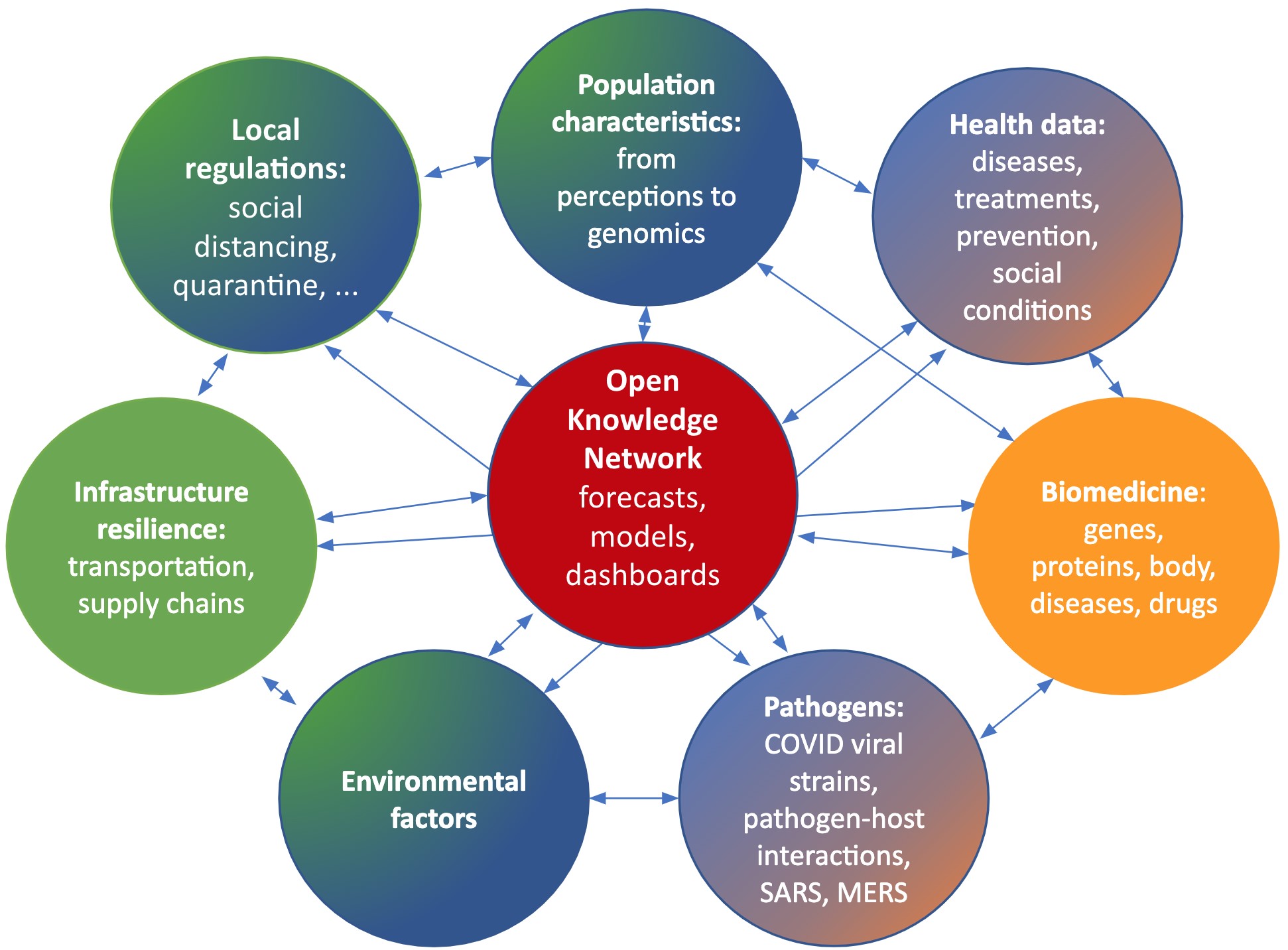



Fighting Covid 19 With Knowledge Graphs
#ff0000 color RGB value is (255,0,0) This hex color code is also a web safe color which is equal to #F00 #ff0000 color name is Red1 color #ff0000 hex color red value is 255, green value is 0 and the blue value of its RGB is 0 Cylindricalcoordinate representations (also known as HSL) of color #ff0000 hue 000 , saturation 100 and the lightness value of ff0000 is 050 More than 45 million people in the US have had confirmed coronavirus infections and more than 745,000 have died of COVID19 Thousands of new cases are reported daily nationwide In the graphicsZachery Mitcham, Director of Network Services at New Hanover Regional Medical Center discusses their protection against Code Red Virus with WECTTV News




Macro Virus Cyberhoot Cyber Library



How To 0wn The Internet In Your Spare Time
South Carolina CountyLevel Data for COVID19 DHEC provides COVID19 data and vaccine updates Monday through Friday at 1 pm Please view the users' manual available here to help navigate through through the dashboard and better understand the data as presented It's important to note that the data within the dashboard is provisional andAuthentication is Computer virus is simply a Code red is a(n) Which of the following can be used for reducing recovery time?The virus spreading in network damaging activities caused by malicious codes are The graphs given below depicts the behaviour of increasing day by day causing harm to society There code red worm First graph shows the number of are various schemes that are designed to defend distinct nct IP address infected by worm second graph against




Where Are Coronavirus Cases Getting Worse Explore Risk Levels County By County Shots Health News Npr



1
The darker the shade, the In this visualization, states that appear in shades of orange have experienced a growth in new cases over the past two weeks States that appear in shades of green have seen declines in cases over the same period of time The shade of the colors indicates the size of each state's growth or decline in new cases;Coronavirus disease (COVID19) Situation Report 1 Philippines 9 March Data reported by the Department of Health on 9 March Highlights A total of 7 new cases tested positive for COVID19 between 6 and 8 March after the first 3 confirmed cases in JanuaryFebruary



News Flash Montgomery County Pa Civicengage



Red Green Yellow Light Abstract Technology Stock Vector Royalty Free
To sign up for updates or to access your subscriber preferences, please enter your contact information below



Chart The Coronavirus Is Almost Everywhere Statista



2




Vector Illustration Red Of Ring And Gears With Malware Bug A Computer Virus Inside On Binary Code Background Vector Illustration Security Technology Concept Eps Clipart Gg Gograph
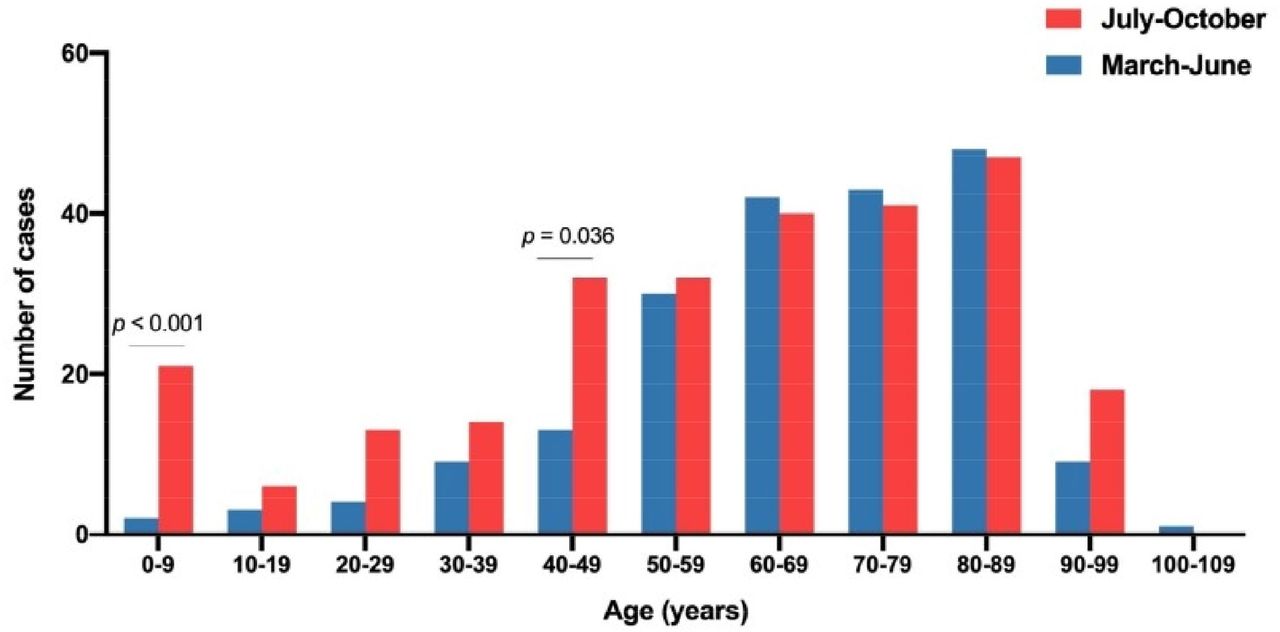



First And Second Waves Of Coronavirus Disease 19 A Comparative Study In Hospitalized Patients In Reus Spain Medrxiv



Musc Covid 19 Epidemiology Intelligence Project Musc Charleston Sc




What To Know About The Coronavirus Outbreak In 17 Charts And Maps World Economic Forum




This Coronavirus App Shows Why Flattening The Curve Matters World Economic Forum




Love Bug S Creator Tracked Down To Repair Shop In Manila c News




Virus Alert Red Virus Alert In A Green Binary Code Canstock




U S Coronavirus Cases And Deaths



How To 0wn The Internet In Your Spare Time




An Early View Of The Economic Impact Of The Pandemic In 5 Charts Imf Blog




Chart Of The Day Update Covid 19 Safety Rules Say Researchers World Economic Forum
/cdn.vox-cdn.com/uploads/chorus_asset/file/19867294/Screen_Shot_2020_04_02_at_1.22.51_PM.png)



The Best Graphs And Data For Tracking The Coronavirus Pandemic The Verge
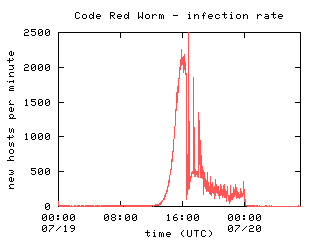



The Spread Of The Code Red Worm Crv2 Caida



Chart How To Decide When To Go Out During Coronavirus Pandemic



Virus Red Writing On Black Skull Binary Code Background Stock Photo Alamy
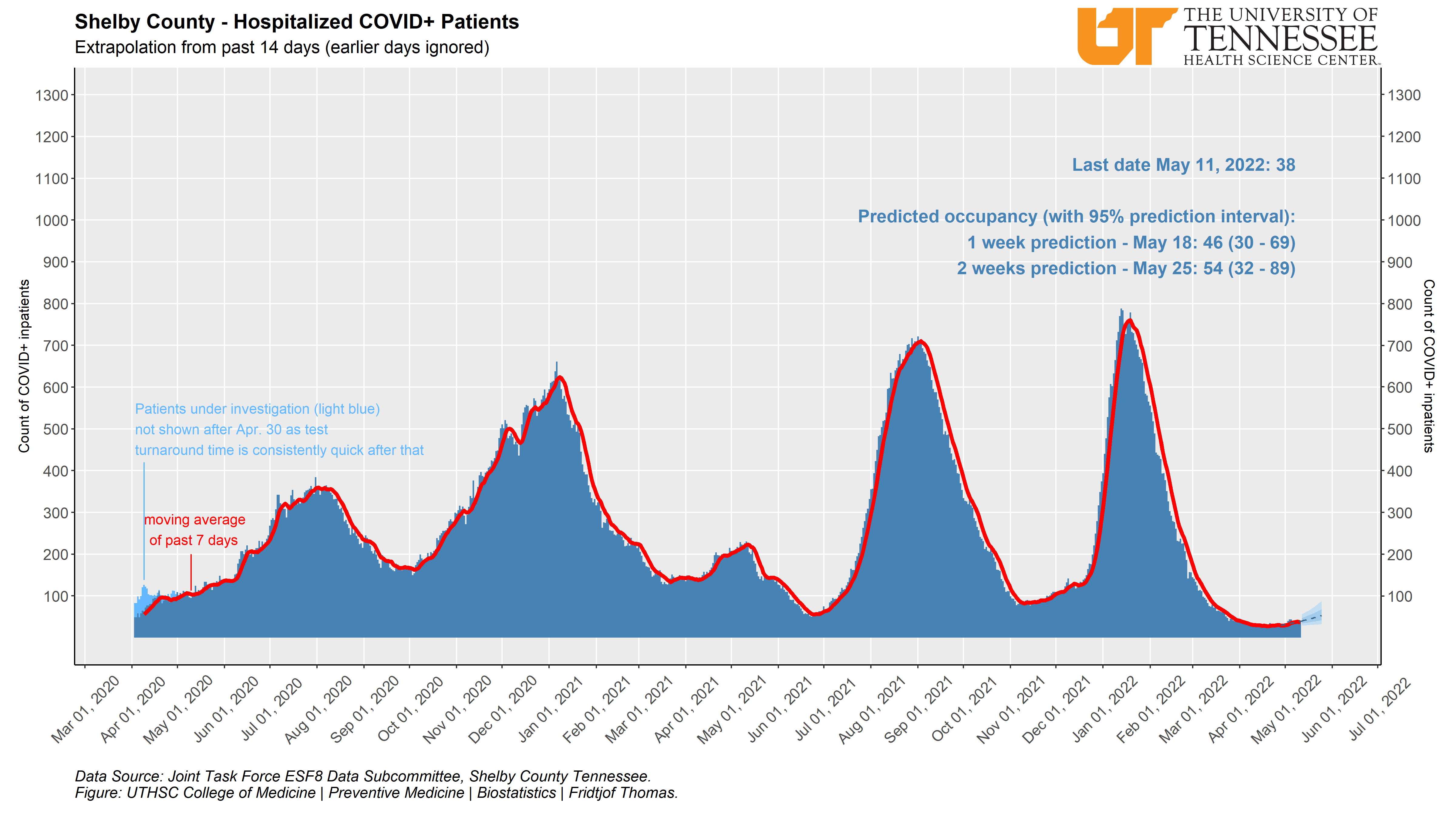



Local Data Coronavirus Disease Information And Resources Uthsc



How To 0wn The Internet In Your Spare Time
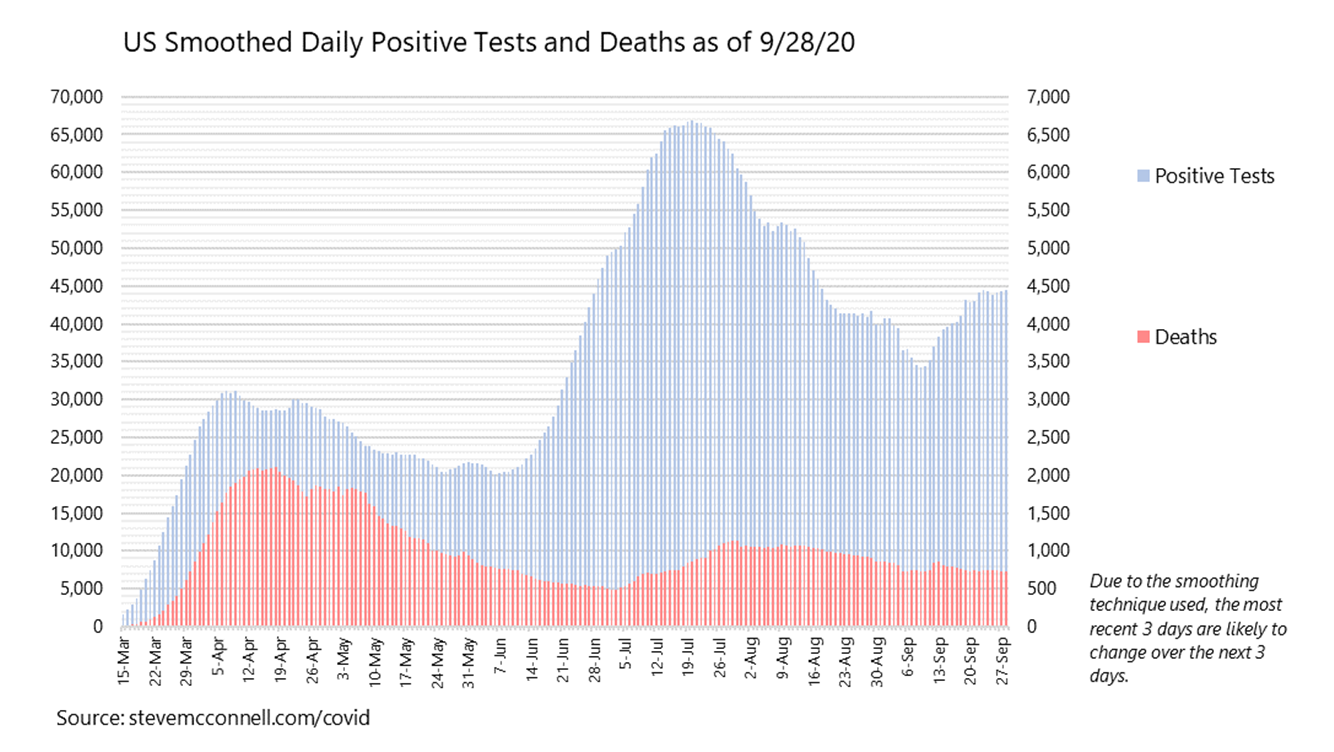



The Graphs You Need To Understand The Covid 19 Pandemic By Steve Mcconnell Towards Data Science



Chart Delta Variant Gains Dominance Around The World Statista




Covid 19 Quiz Do You Really Know The Facts About Coronavirus Johnson Johnson




Code Red No Survivors Project By Joshua Sargent Ii Kickstarter



Hiv Aids Our World In Data




Computer Virus Binary Code Wire With Red Viruses Stock Photo Download Image Now Istock




Red Of Ring And Gears With Malware Bug A Computer Virus Inside On Binary Code Background Vector Illustration Security Technology Concept Royalty Free Cliparts Vectors And Stock Illustration Image




Covid Who Is Getting The Pfizer Vaccine First And When Can I Have It c News




To Navigate Risk In A Pandemic You Need A Color Coded Chart Wired



Coronavirus Faq Union Township Nj Official Website
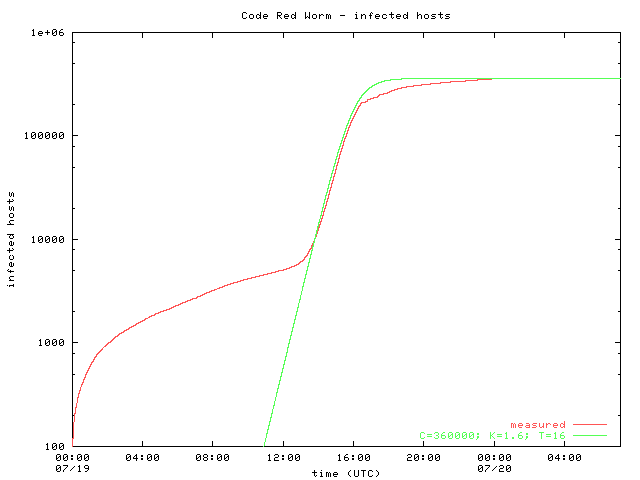



The Spread Of The Code Red Worm Crv2 Caida
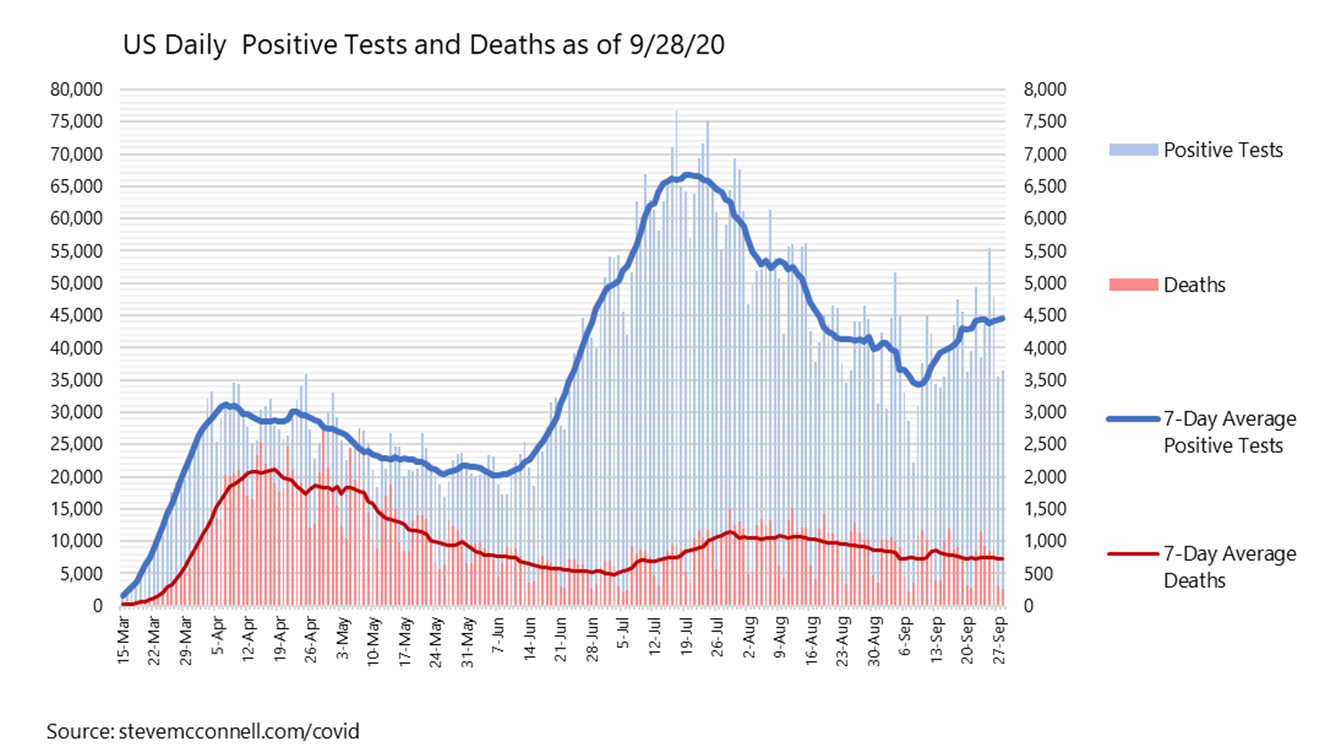



The Graphs You Need To Understand The Covid 19 Pandemic By Steve Mcconnell Towards Data Science




10 Phishing Email Examples You Need To See




Study And Overview Of The Novel Corona Virus Disease Covid 19 Sciencedirect




Spirals Of Blue Binary Code And The Word Virus Repeated Many Times In Red High Res Stock Photo Getty Images
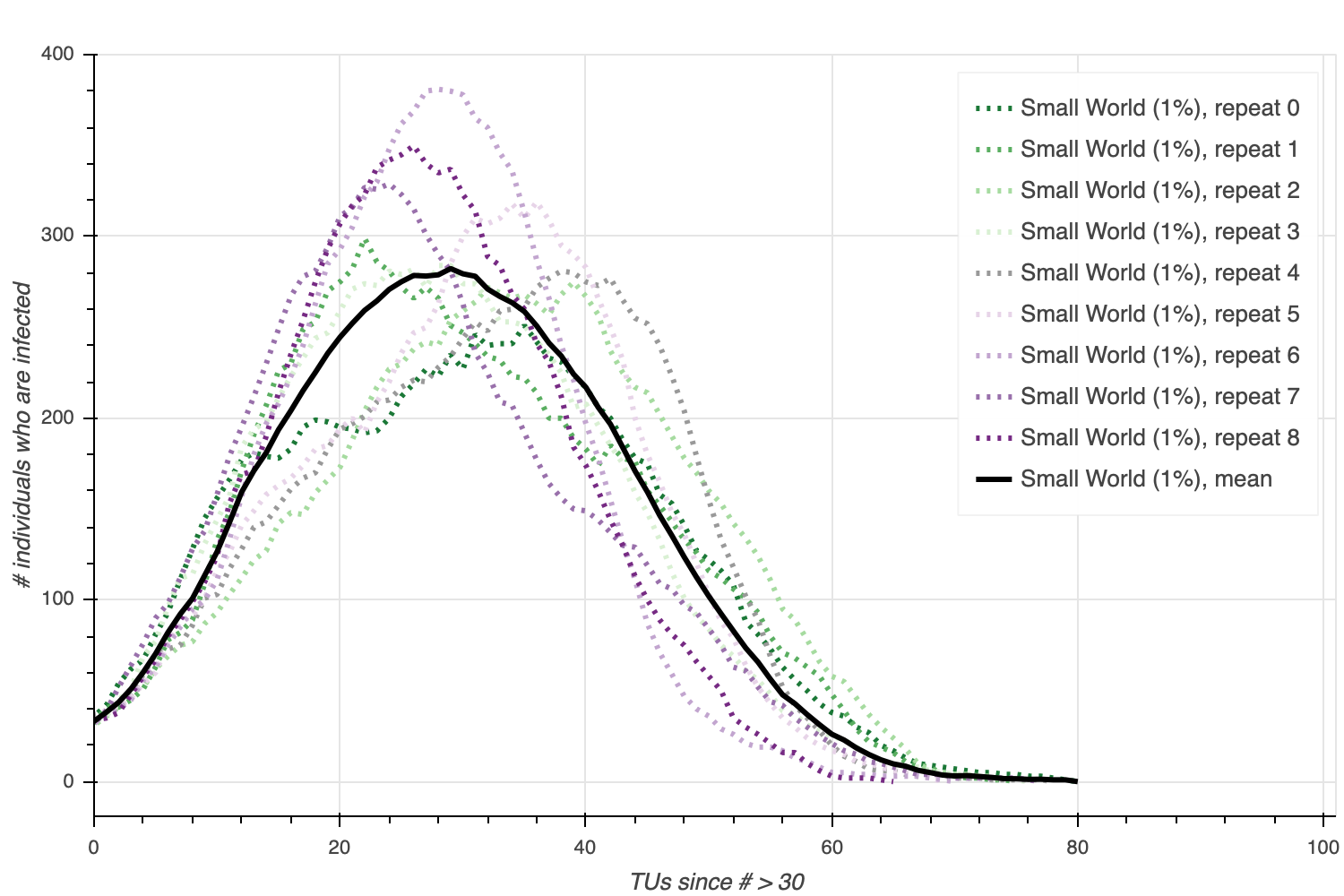



The Social Graphs In Viral Growth By Anders Ohrn Towards Data Science




Overreacting To Zotob Or Under Reacting Before Aug 25 05



Fao Asf Situation Update African Swine Fever Asf Fao Emergency Prevention System For Animal Health Empres Ah




Tracking The Spread Of Coronavirus With Graph Databases




Mapping Covid 19 Dartmouth Atlas Of Health Care



Coronavirus Collage Balloon Icon With Grunge Code Red Stamp Coronavirus Collage Balloon Icon And Round Corroded Stamp Seal Canstock




Twindemic Averted Not Much Flu In Mass And Record Low Rates Across The Nation Wbur News




The Number Of Distinct Ip Addresses Infected By Code Red V2 During Its Download Scientific Diagram
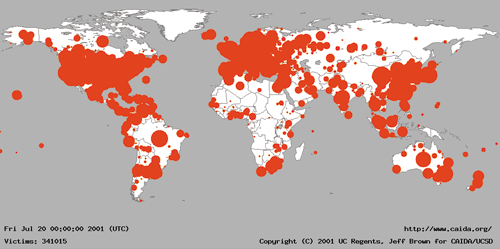



Caida Analysis Of Code Red Caida




Virus Corona Coronavirus Free Vector Graphic On Pixabay




Amazon Com Code Red The Gurinman King Joshua Books




Pdf Code Red A Case Study On The Spread And Victims Of An Internet Worm Semantic Scholar




Coronavirus Virus Red Free Vector Graphic On Pixabay
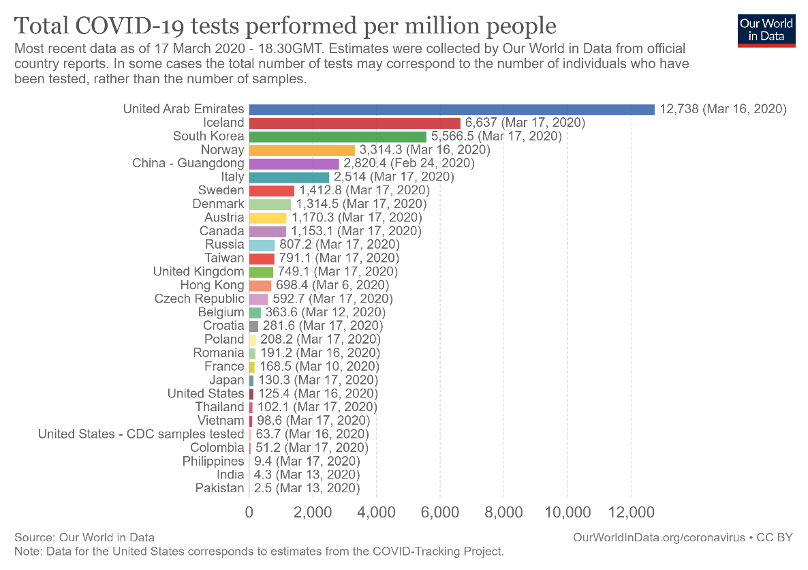



Covid 19 Information Problems And Digital Surveillance Center For Global Development
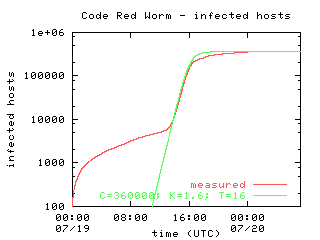



The Spread Of The Code Red Worm Crv2 Caida




Covid In North Carolina Maps Graphs Cases And Restrictions



Directed Graph Epidemiological Models Of Computer Viruses Presented By Kelvin Weiguo Jin We Adapt The Techniques Of Mathematical Epidemiology To Ppt Download




Steven Universe Virus Infected Pearl By 6the6overlord6 On Deviantart
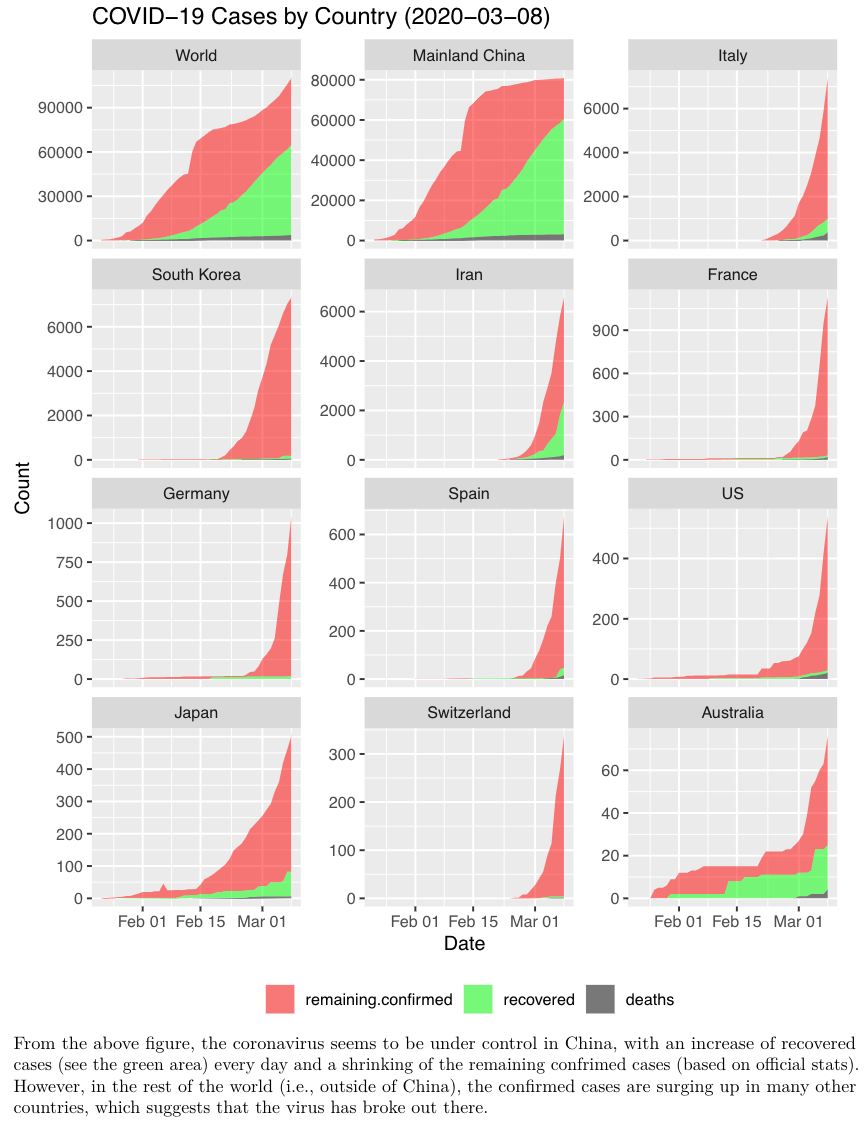



Top 100 R Resources On Novel Covid 19 Coronavirus Stats And R



2



Beissen Gedanken Pc Viruses And Worms




The Graphs You Need To Understand The Covid 19 Pandemic By Steve Mcconnell Towards Data Science




The Wannacry Virus Is Among Red Binary Code And Ransomware Virus Computer Attack Stock Vector Illustration Of Antivirus Firewall
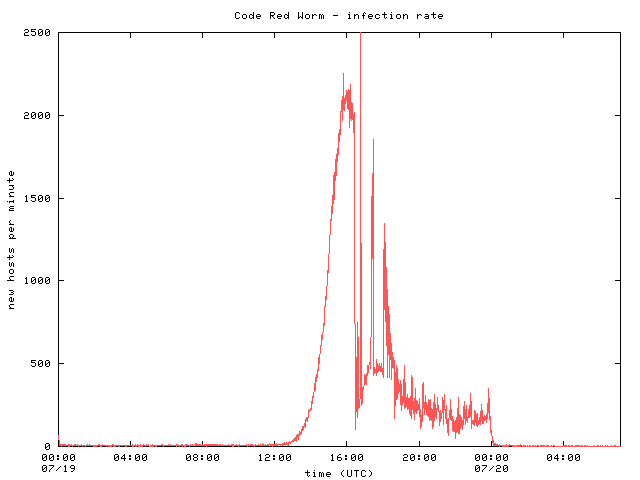



The Spread Of The Code Red Worm Crv2 Caida



2
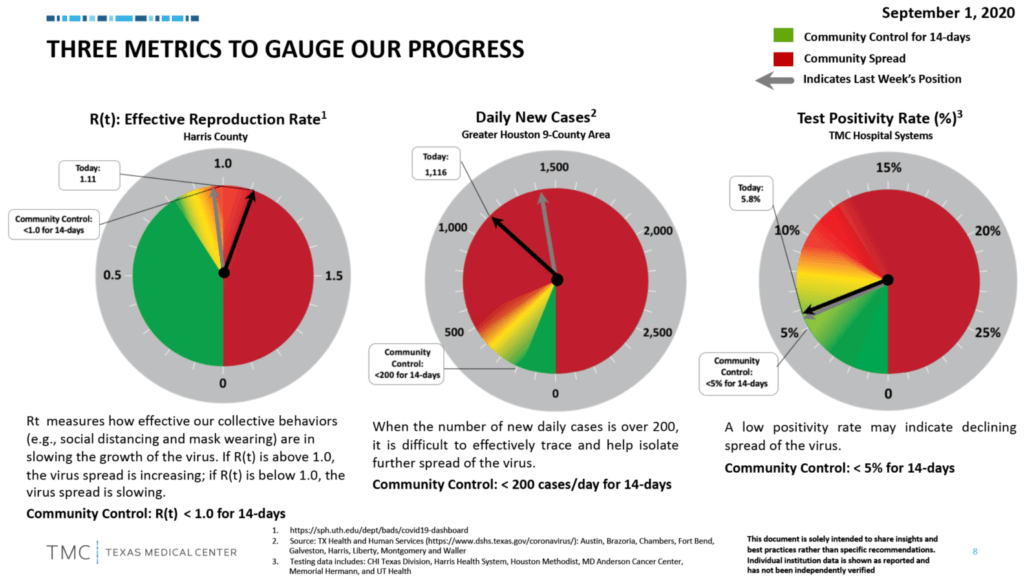



Coronavirus A Texas Medical Center Continuing Update Tmc News



Code Red Et Al



Big Red Data Crunching Numbers To Fight Covid 19 And More Cornell Chronicle




Freedom In The World 21 Democracy Under Siege Freedom House




Detailed Illustration Of Data Tunnel With Binary Code With Computer Virus Detection Stock Photo Picture And Royalty Free Image Image




10 Most Dangerous Computer Viruses Education Today News
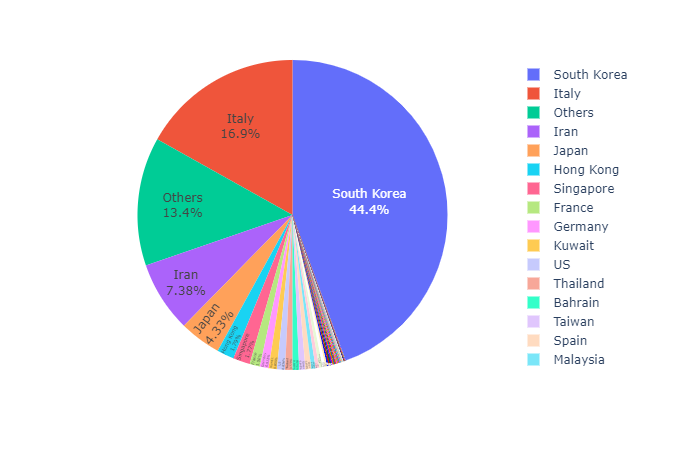



Coronavirus Data Visualizations Using Plotly By Terence Shin Towards Data Science



Chart The State Of The Third Wave In Europe Statista
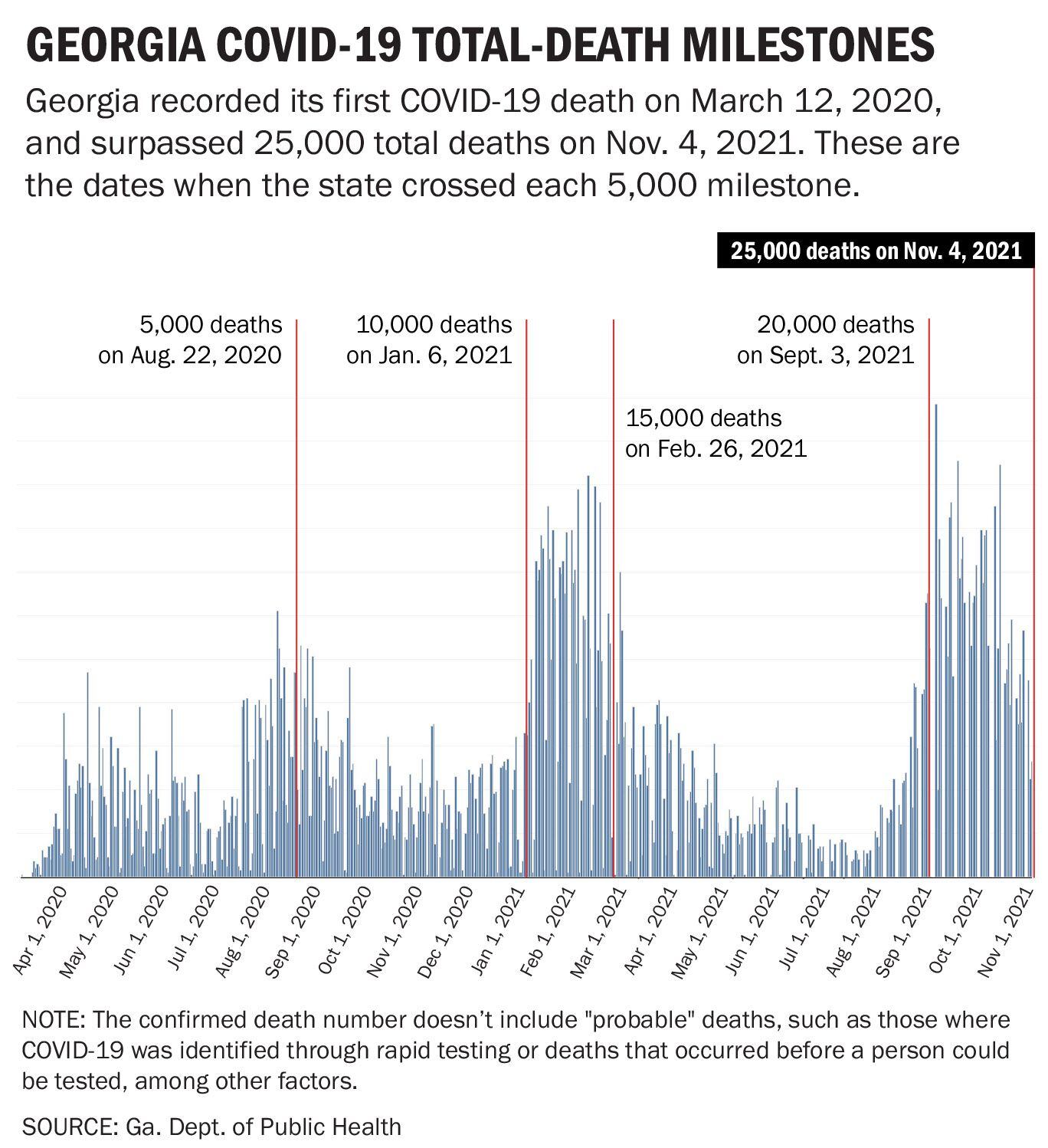



Ahpb436xeptc0m




Code Red Virus High Resolution Stock Photography And Images Alamy




Solved 13 The Figure Below Shows The Spread Of The Code Red Chegg Com



Is The Coronavirus Mutating Yes Here S Why You Don T Need To Panic Science News
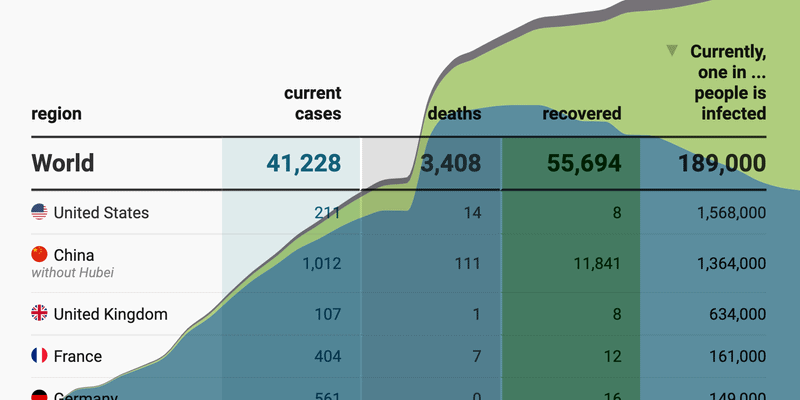



17 Or So Responsible Live Visualizations About The Coronavirus For You To Use Datawrapper Blog
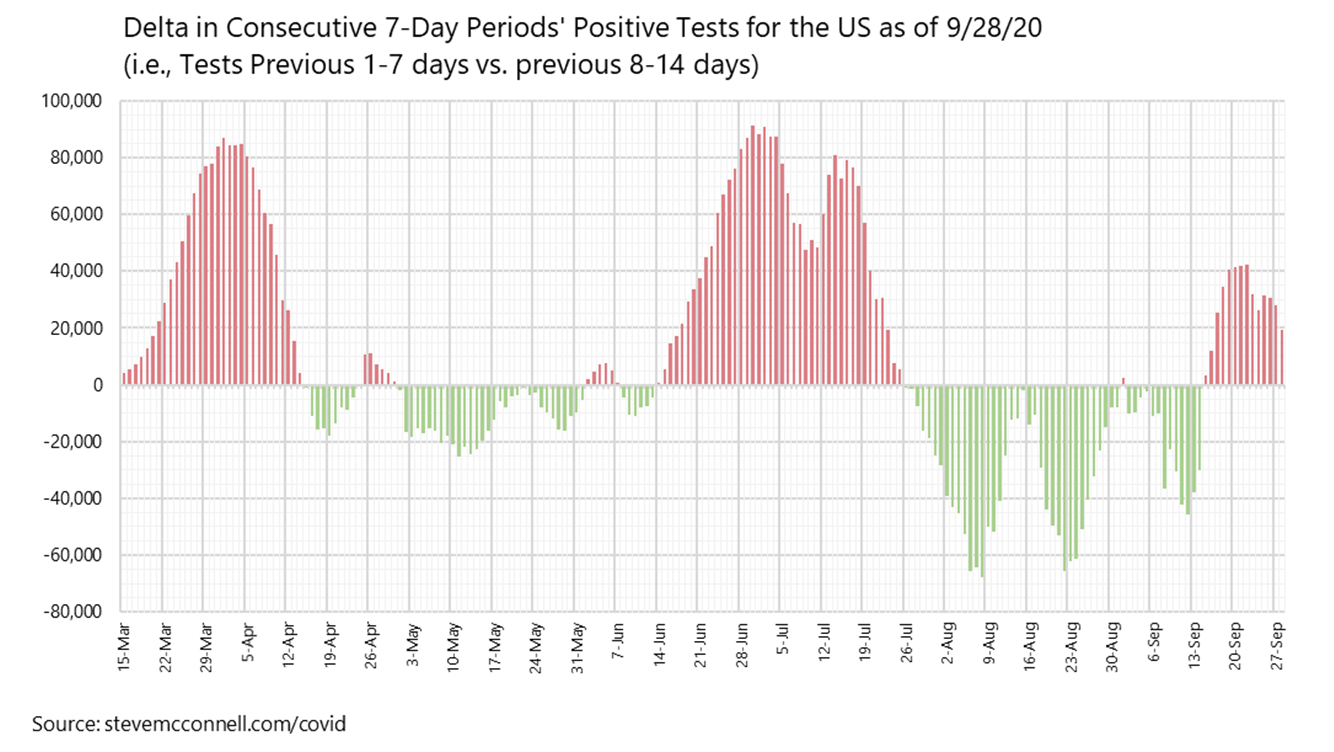



The Graphs You Need To Understand The Covid 19 Pandemic By Steve Mcconnell Towards Data Science




Coronavirus And Exponential Growth Updated 4 Seti Institute



La County Daily Covid 19 Data La County Department Of Public Health


